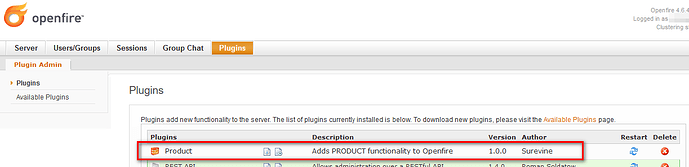
This security bypass is already being actively exploited in the wild. I found additional admin users created and also a suspicious plugin installed, named “Product” with author “Surevine” (ironically credited for helping disclose this vuln):
Decompiling the plugin jar I found that it deploys a JSP-based remote web shell endpoint intended to allow attackers to execute arbitrary commands on the server. Attempting to delete the plugin from the Openfire UI fails; to remove the plugin completely you need to stop the Openfire service, delete the product.jar and product folder from the plugins directory manually, and restart.
Check the value of the admin.authorizedJIDs system property and look for suspicious additional usernames added. Edit the property to remove any that should not be there. Then delete the corresponding user accounts.
View the Openfire security audit log and the deployment of the plugin and additional admin logins will also be visible.
Best advice: Never open the Openfire admin web page ports 9090 and 9091 to the internet, and if you have to then make sure you firewall them to allow access only from authorized IP addresses.