right and the you pull in every account created by AD as well as user accounts, every group, computer, etc. You then are forced to use filters to limited what is shown. Filters that slow performance. It can be done that way, but why not if you are uncertain about the functionality of AD rework it so you are sure.
It wasn’t bad support, i was just trying to get it to work period. If he can get it to work, then he can starts setting up AD OU’s and fine tune what gets pulled in through the BASE DN.
I typo’d here:
**
**
port should be 389 not 339
Ultimately if you are unfamiliar with AD it is going to be hard to help you without a clearly defined structure. If you could do these steps:
- Create a new AD user in the default Users CN of AD. THis user is to be used with LDAP binding (openfire’s AdminDN). The user does not need to be a domain admin.
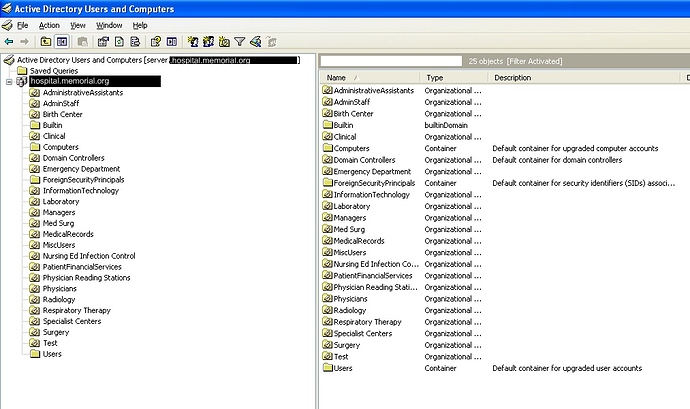
- Take a screenshot of the AD tree fully expanded from the MMC Active Directory Users & Computers. You can edit the domain out if you like for security. If you do edit it out we need to know a generic representation of the domain (e.x. microsoft.local could be domain.local) Post the pic here.
I’m sure there are tons of opinions on configuring AD, that’s a really FLAT AD structure. I’ve configured ours such as
COM
—domain
------Servers Group
---------OU’s for departments/application role
------Desktops Group
---------OU’s for departments
------Distribution Groups
---------OU’s for departments
------Secutiry Groups
---------OU’s for departments
------User Groups (not the default one)
---------Users (BaseDN points here)
------------OU’s for departments
---------Consultants and Vendors
------------OU’s for departments
Everyone is allowed openfire usage here.
My BaseDN looks like: OU=“Users”,OU=“User Groups”,DC="",DC=“com”
Your BaseDN should look something like: dc=hospital,dc=memorial,dc=org (edited to reflect todd’s correct basedn)
But as Todd pointed out, you’d be sucking EVERYTHING across into openfire.
(also note my typo in my original post, port 389 not 339)
You base DN should not be pointing to a specific server CN nor should there be any spaces in the string. You have a space after hospital.
your BaseDN should be dc=hospital,dc=memorial,dc=org
Thanks todd. cut and pasted way too fast. changed my post so as not to confuse him.
You should definitely look at restructuring those OUs. Everything thing is in the root with the Default CNs. Making parent OUs and nesting stuff will give you more control. See my example above.
It’s a work in progress. You’d not imagine (well, maybe you can) the fight to get it to this stage so far. The fear of AD structure modifications screwing everything up is almost as bad as my son’s school over H1N1 now.
Openfire is the only application using LDAP at the moment. So, i’m a bit pressed on getting much further than this at the moment. As new applications come in and I can prove a need for better structuring, that’s when my argument to modify gets attention.
The spaces are a product of the image editing. Sorry about that.
Ken did you get this working?
you have your base dn now? dc=hospital,dc=memorial,dc=org
create a user in AD to use as an admin user for openfire. and find the DN of that user. It will look somthing like this: CN=openfireadmin,OU=serviceusers,DC=hospital,DC=memorial,DC=org
Now you’ll need to filter for users and groups. For this you’ll need to know a little bit about LDAP searching.
For my environment I made a new group just for openfire. say it’s openfireallow. every user and group (that will appear in the roster) will need to be a member. Your ldap search filters will need to look something like this
user filter: (&(objectClass=organizationalPerson)(memberOf=CN=openfireallow,OU=DomainGroups,D C=hospital,DC=memorial,DC=org))
group filter: (&(objectClass=group)(memberOf=CN=openfireallow,OU=DomainGroups,DC=hospital,DC=m emorial,DC=org))
now put your users into the openfireallow group and create more groups for the roster display. Make the new roster groups a member of the openfireallow group and make the users for each roster members of the group.
While you’re learning LDAP and AD I recommend getting an LDAP browser like the Softerra LDPA Browser ( free download of the 2.6 version from here) http://www.ldapadministrator.com/download.htm
AD and LDAP are not that hard but it will take you some studying to get the hang of it. Looking at the structure may help.
Good Luck,
chrisj
Wow, Thanks Chris,
To answer your question…no I haven’t got it working quite yet. This has been a much bigger challenge then I had expected. Even if/after I get it working the next challenge is to figure out how to install the client on my networked PC’s. Today I will be busy with a new antivirus rollout, I’ll try to get back to this later this week.
Thanks for your help.
Ken