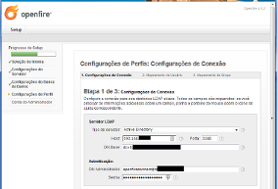
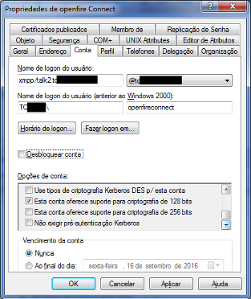
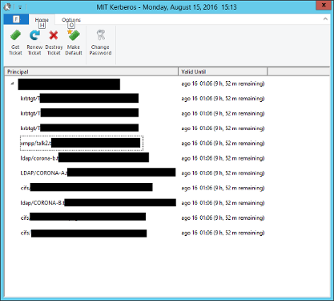
I used today the 2.7.7 version and is attached the file warn spark log. And also the krb5.ini file used. And MIT Kerberos Ticket Manager screen showing that XMPP is mounted. I hope it’s this way.
Is it any setting in Openfire that this trouble?

File krb5.ini:
[libdefaults]
default_realm = TOO.DOMINIO.COM.BR
[realms]
TOO.DOMINIO.COM.BR = {
kdc = corona-a.too.dominio.com.br
kdc = corona-b.too.dominio.com.br
admin_server = corona-a.too.dominio.com.br
default_domain = too.dominio.com.br
}
[domain_realms]
too.dominio.com.br = TOO.DOMINIO.COM.BR
.too.dominio.com.br = TOO.DOMINIO.COM.BR
Warn file:
ago 15, 2016 3:11:11 PM org.jivesoftware.spark.util.log.Log warning
WARNING: Exception in Login:
java.lang.reflect.InvocationTargetException
at java.awt.EventQueue.invokeAndWait(Unknown Source)
at java.awt.EventQueue.invokeAndWait(Unknown Source)
at org.jivesoftware.LoginDialog$LoginPanel.login(LoginDialog.java:1103)
at org.jivesoftware.LoginDialog$LoginPanel.access$1400(LoginDialog.java:362)
at org.jivesoftware.LoginDialog$LoginPanel$4.construct(LoginDialog.java:900)
at org.jivesoftware.spark.util.SwingWorker$2.run(SwingWorker.java:141)
at java.lang.Thread.run(Unknown Source)
Caused by: java.lang.IllegalArgumentException: Can’t initialize the configured debugger!
at org.jivesoftware.smack.Connection.initDebugger(Connection.java:792)
at org.jivesoftware.smack.XMPPConnection.initReaderAndWriter(XMPPConnection.java:7 42)
at org.jivesoftware.smack.XMPPConnection.initConnection(XMPPConnection.java:619)
at org.jivesoftware.smack.XMPPConnection.connectUsingConfiguration(XMPPConnection. java:604)
at org.jivesoftware.smack.XMPPConnection.connect(XMPPConnection.java:1022)
at org.jivesoftware.LoginDialog$LoginPanel$5.run(LoginDialog.java:1108)
at java.awt.event.InvocationEvent.dispatch(Unknown Source)
at java.awt.EventQueue.dispatchEventImpl(Unknown Source)
at java.awt.EventQueue.access$500(Unknown Source)
at java.awt.EventQueue$3.run(Unknown Source)
at java.awt.EventQueue$3.run(Unknown Source)
at java.security.AccessController.doPrivileged(Native Method)
at java.security.ProtectionDomain$JavaSecurityAccessImpl.doIntersectionPrivilege(U nknown Source)
at java.awt.EventQueue.dispatchEvent(Unknown Source)
at java.awt.EventDispatchThread.pumpOneEventForFilters(Unknown Source)
at java.awt.EventDispatchThread.pumpEventsForFilter(Unknown Source)
at java.awt.EventDispatchThread.pumpEventsForHierarchy(Unknown Source)
at java.awt.EventDispatchThread.pumpEvents(Unknown Source)
at java.awt.EventDispatchThread.pumpEvents(Unknown Source)
at java.awt.EventDispatchThread.run(Unknown Source)
Caused by: java.lang.reflect.InvocationTargetException
at sun.reflect.NativeConstructorAccessorImpl.newInstance0(Native Method)
at sun.reflect.NativeConstructorAccessorImpl.newInstance(Unknown Source)
at sun.reflect.DelegatingConstructorAccessorImpl.newInstance(Unknown Source)
at java.lang.reflect.Constructor.newInstance(Unknown Source)
at org.jivesoftware.smack.Connection.initDebugger(Connection.java:787)
… 19 more
Caused by: java.lang.IncompatibleClassChangeError: class org.jivesoftware.phone.client.action.PhoneActionIQProvider has interface org.jivesoftware.smack.provider.IQProvider as super class
at java.lang.ClassLoader.defineClass1(Native Method)
at java.lang.ClassLoader.defineClass(Unknown Source)
at java.security.SecureClassLoader.defineClass(Unknown Source)
at java.net.URLClassLoader.defineClass(Unknown Source)
at java.net.URLClassLoader.access$100(Unknown Source)
at java.net.URLClassLoader$1.run(Unknown Source)
at java.net.URLClassLoader$1.run(Unknown Source)
at java.security.AccessController.doPrivileged(Native Method)
at java.net.URLClassLoader.findClass(Unknown Source)
at java.lang.ClassLoader.loadClass(Unknown Source)
at sun.misc.Launcher$AppClassLoader.loadClass(Unknown Source)
at java.lang.ClassLoader.loadClass(Unknown Source)
at java.lang.Class.forName0(Native Method)
at java.lang.Class.forName(Unknown Source)
at org.jivesoftware.smack.provider.ProviderManager.initialize(ProviderManager.java :193)
at org.jivesoftware.smack.provider.ProviderManager.(ProviderManager.java:436 )
at org.jivesoftware.smack.provider.ProviderManager.getInstance(ProviderManager.jav a:134)
at org.jivesoftware.smackx.debugger.EnhancedDebuggerWindow.createDebug(EnhancedDeb uggerWindow.java:227)
at org.jivesoftware.smackx.debugger.EnhancedDebuggerWindow.showNewDebugger(Enhance dDebuggerWindow.java:125)
at org.jivesoftware.smackx.debugger.EnhancedDebuggerWindow.addDebugger(EnhancedDeb uggerWindow.java:115)
at org.jivesoftware.smackx.debugger.EnhancedDebugger.(EnhancedDebugger.java: 148)
… 24 more
ago 15, 2016 3:11:22 PM org.jivesoftware.spark.util.log.Log warning
WARNING: Exception in Login:
SASL authentication failed:
– caused by: javax.security.sasl.SaslException: GSS initiate failed [Caused by GSSException: No valid credentials provided (Mechanism level: Server not found in Kerberos database (7))]
at org.jivesoftware.smack.sasl.SASLMechanism.authenticate(SASLMechanism.java:196)
at org.jivesoftware.smack.sasl.SASLMechanism.authenticate(SASLMechanism.java:152)
at org.jivesoftware.smack.SASLAuthentication.authenticate(SASLAuthentication.java: 324)
at org.jivesoftware.smack.XMPPConnection.login(XMPPConnection.java:243)
at org.jivesoftware.LoginDialog$LoginPanel.login(LoginDialog.java:1138)
at org.jivesoftware.LoginDialog$LoginPanel.access$1400(LoginDialog.java:362)
at org.jivesoftware.LoginDialog$LoginPanel$4.construct(LoginDialog.java:900)
at org.jivesoftware.spark.util.SwingWorker$2.run(SwingWorker.java:141)
at java.lang.Thread.run(Unknown Source)
Nested Exception:
javax.security.sasl.SaslException: GSS initiate failed [Caused by GSSException: No valid credentials provided (Mechanism level: Server not found in Kerberos database (7))]
at com.sun.security.sasl.gsskerb.GssKrb5Client.evaluateChallenge(Unknown Source)
at org.jivesoftware.smack.sasl.SASLMechanism.authenticate(SASLMechanism.java:192)
at org.jivesoftware.smack.sasl.SASLMechanism.authenticate(SASLMechanism.java:152)
at org.jivesoftware.smack.SASLAuthentication.authenticate(SASLAuthentication.java: 324)
at org.jivesoftware.smack.XMPPConnection.login(XMPPConnection.java:243)
at org.jivesoftware.LoginDialog$LoginPanel.login(LoginDialog.java:1138)
at org.jivesoftware.LoginDialog$LoginPanel.access$1400(LoginDialog.java:362)
at org.jivesoftware.LoginDialog$LoginPanel$4.construct(LoginDialog.java:900)
at org.jivesoftware.spark.util.SwingWorker$2.run(SwingWorker.java:141)
at java.lang.Thread.run(Unknown Source)
Caused by: GSSException: No valid credentials provided (Mechanism level: Server not found in Kerberos database (7))
at sun.security.jgss.krb5.Krb5Context.initSecContext(Unknown Source)
at sun.security.jgss.GSSContextImpl.initSecContext(Unknown Source)
at sun.security.jgss.GSSContextImpl.initSecContext(Unknown Source)
… 10 more
Caused by: KrbException: Server not found in Kerberos database (7)
at sun.security.krb5.KrbTgsRep.(Unknown Source)
at sun.security.krb5.KrbTgsReq.getReply(Unknown Source)
at sun.security.krb5.KrbTgsReq.sendAndGetCreds(Unknown Source)
at sun.security.krb5.internal.CredentialsUtil.serviceCreds(Unknown Source)
at sun.security.krb5.internal.CredentialsUtil.acquireServiceCreds(Unknown Source)
at sun.security.krb5.Credentials.acquireServiceCreds(Unknown Source)
… 13 more
Caused by: KrbException: Identifier doesn’t match expected value (906)
at sun.security.krb5.internal.KDCRep.init(Unknown Source)
at sun.security.krb5.internal.TGSRep.init(Unknown Source)
at sun.security.krb5.internal.TGSRep.(Unknown Source)
… 19 more