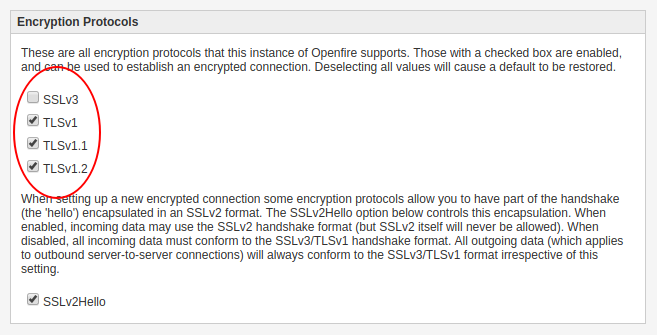
Following is OF v4.1.3 logs when Client is communicating with TLS 1.2 explicitly.
What is missing from server side setting?
I only enabled TLS 1.2 in encryption protocols and used same TLS 1.2 in our client.
Can somebody please guide me?
> 2019.06.18 10:12:40 DEBUG [NioProcessor-1]: org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event SESSION_OPENED to session 3
> Queue : [SESSION_OPENED, ]
>
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-2]: org.apache.mina.core.filterchain.IoFilterEvent - Firing a SESSION_OPENED event for session 3
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-2]: org.apache.mina.core.filterchain.IoFilterEvent - Event SESSION_OPENED has been fired for session 3
> 2019.06.18 10:12:40 DEBUG [NioProcessor-1]: org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_RECEIVED to session 3
> Queue : [MESSAGE_RECEIVED, ]
>
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-3]: org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_RECEIVED event for session 3
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-3]: org.apache.mina.filter.codec.ProtocolCodecFilter - Processing a MESSAGE_RECEIVED for session 3
> 2019.06.18 10:12:40 DEBUG [NioProcessor-1]: org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_SENT to session 3
> Queue : [MESSAGE_SENT, ]
>
> 2019.06.18 10:12:40 TRACE [socket_c2s-thread-3]: org.jivesoftware.openfire.net.SASLAuthentication - Cannot support 'ANONYMOUS' as it has been disabled by configuration.
> 2019.06.18 10:12:40 TRACE [socket_c2s-thread-3]: org.jivesoftware.openfire.net.SASLAuthentication - Cannot support 'SCRAM-SHA-1' as the AuthFactory that's in used does not support password retrieval nor SCRAM.
> 2019.06.18 10:12:40 TRACE [socket_c2s-thread-3]: org.jivesoftware.openfire.net.SASLAuthentication - Cannot support 'GSSAPI' as the 'sasl.gssapi.config' property has not been defined.
> 2019.06.18 10:12:40 TRACE [socket_c2s-thread-3]: org.jivesoftware.openfire.net.SASLAuthentication - Cannot support 'CRAM-MD5' as the AuthFactory that's in used does not support password retrieval.
> 2019.06.18 10:12:40 TRACE [socket_c2s-thread-3]: org.jivesoftware.openfire.net.SASLAuthentication - Cannot support 'DIGEST-MD5' as the AuthFactory that's in used does not support password retrieval.
> 2019.06.18 10:12:40 TRACE [socket_c2s-thread-3]: org.jivesoftware.openfire.net.SASLAuthentication - Cannot support 'JIVE-SHAREDSECRET' as it has been disabled by configuration.
> 2019.06.18 10:12:40 DEBUG [NioProcessor-1]: org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_SENT to session 3
> Queue : [MESSAGE_SENT, , MESSAGE_SENT, ]
>
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-3]: org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_RECEIVED has been fired for session 3
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-3]: org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_SENT event for session 3
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-3]: org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_SENT has been fired for session 3
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-3]: org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_SENT event for session 3
> 2019.06.18 10:12:40 DEBUG [socket_c2s-thread-3]: org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_SENT has been fired for session 3
> 2019.06.18 10:12:41 DEBUG [NioProcessor-1]: org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event MESSAGE_RECEIVED to session 3
> Queue : [MESSAGE_RECEIVED, ]
>
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.core.filterchain.IoFilterEvent - Firing a MESSAGE_RECEIVED event for session 3
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.filter.codec.ProtocolCodecFilter - Processing a MESSAGE_RECEIVED for session 3
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.jivesoftware.openfire.keystore.OpenfireX509TrustManager - Constructed trust manager. Number of trusted issuers: 0, accepts self-signed: false, checks validity: true
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.jivesoftware.openfire.keystore.OpenfireX509TrustManager - Constructed trust manager. Number of trusted issuers: 0, accepts self-signed: false, checks validity: true
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.filter.ssl.SslFilter - Adding the SSL Filter tls to the chain
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.filter.ssl.SslHandler - Session Server[3](no sslEngine) Initializing the SSL Handler
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.filter.ssl.SslHandler - Session Server[3](no sslEngine) SSL Handler Initialization done.
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.filter.ssl.SslFilter - Session Server[3](ssl...) : Starting the first handshake
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.filter.ssl.SslHandler - Session Server[3](ssl...) processing the NEED_UNWRAP state
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.filter.ssl.SslFilter - Session Server[3](ssl...): Writing Message : WriteRequest: HeapBuffer[pos=0 lim=50 cap=64: 3C 70 72 6F 63 65 65 64 20 78 6D 6C 6E 73 3D 22...]
> 2019.06.18 10:12:41 DEBUG [socket_c2s-thread-2]: org.apache.mina.core.filterchain.IoFilterEvent - Event MESSAGE_RECEIVED has been fired for session 3
> 2019.06.18 10:12:41 DEBUG [NioProcessor-1]: org.apache.mina.filter.ssl.SslFilter - Session Server[3](ssl...): Message received : HeapBuffer[pos=0 lim=187 cap=1024: 16 03 03 00 B6 01 00 00 B2 03 03 5D 08 B9 19 63...]
> 2019.06.18 10:12:41 DEBUG [NioProcessor-1]: org.apache.mina.filter.ssl.SslHandler - Session Server[3](ssl...) Processing the received message
> 2019.06.18 10:12:41 DEBUG [NioProcessor-1]: org.apache.mina.filter.ssl.SslHandler - Session Server[3](ssl...) processing the NEED_UNWRAP state
> 2019.06.18 10:12:41 DEBUG [NioProcessor-1]: org.apache.mina.filter.ssl.SslHandler - Session Server[3](ssl...) processing the NEED_TASK state
> 2019.06.18 10:12:41 DEBUG [NioProcessor-1]: org.apache.mina.filter.ssl.SslHandler - Session Server[3](ssl...) processing the NEED_UNWRAP state
> 2019.06.18 10:12:41 DEBUG [NioProcessor-1]: org.apache.mina.filter.ssl.SslFilter - Session Server[3](ssl...): Processing the SSL Data
> 2019.06.18 10:14:08 DEBUG [TaskEngine-pool-2]: org.logicalcobwebs.proxool.openfire - Closing statement 1ad298 (belonging to connection 1) automatically
> 2019.06.18 10:15:41 DEBUG [NioProcessor-1]: org.apache.mina.filter.executor.OrderedThreadPoolExecutor - Adding event SESSION_IDLE to session 3
> Queue : [SESSION_IDLE, ]
>
> 2019.06.18 10:15:41 DEBUG [socket_c2s-thread-3]: org.apache.mina.core.filterchain.IoFilterEvent - Firing a SESSION_IDLE event for session 3
> 2019.06.18 10:15:41 DEBUG [socket_c2s-thread-3]: org.jivesoftware.openfire.nio.ClientConnectionHandler - ConnectionHandler: Pinging connection that has been idle: org.jivesoftware.openfire.nio.NIOConnection@1868301 MINA Session: (0x00000003: nio socket, server, /115.114.134.252:32361 => /10.0.0.4:5222)
> 2019.06.18 10:15:41 DEBUG [socket_c2s-thread-3]: org.apache.mina.filter.ssl.SslFilter - Session Server[3](ssl...): Writing Message : WriteRequest: HeapBuffer[pos=0 lim=147 cap=4096: 3C 69 71 20 74 79 70 65 3D 22 67 65 74 22 20 69...]
> 2019.06.18 10:15:41 DEBUG [socket_c2s-thread-3]: org.apache.mina.core.filterchain.IoFilterEvent - Event SESSION_IDLE has been fired for session 3