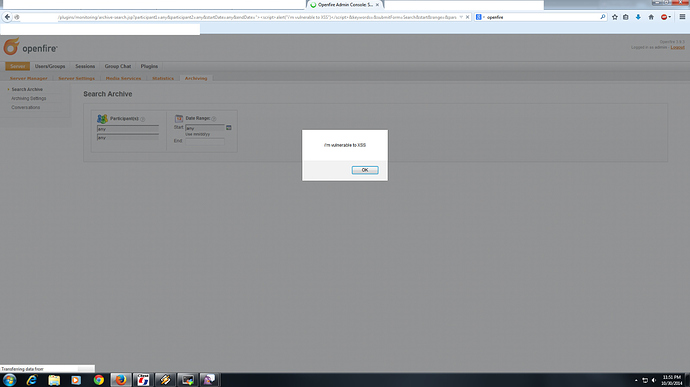
In the admin panel of openfire, if you go to Archiving to start a search for a conversation you will have a url something like this:
The folowing parameters are vulnerable to Reflected XSS(Cross Site Scripting):
participant1
participant2
startDate
endDate
keywords
Proof of Concept:
You can see in the top right that it is the latest version of openfire.
Thanks