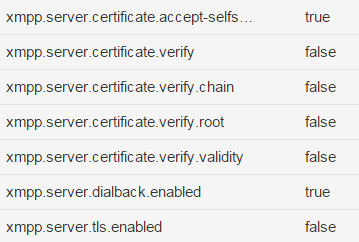
I have been trying to get a good rule set for iptables for OF. I have two VPS servers each running CentOS 7 x64 with OF 3.10.2 each with a static public IP. I have added each to each others /etc/hosts file and I can ping each other when I have iptables running. I can also connect to each other using telnet over port 5269… But, OF throws this warning:
2015.10.14 18:01:10 org.jivesoftware.openfire.session.LocalOutgoingServerSession - Fail to connect to chat.us.east for chat.us.west
The crazy part of it is, only the s2s is failing, it works just fine when iptables is stopped.
nmap reports:
Nmap scan report for chat.us.west (216.158.224.246)
Host is up (0.000033s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
5222/tcp open xmpp-client
5269/tcp open xmpp-server
9090/tcp open zeus-admin
9091/tcp open xmltec-xmlmail
which is what I expected.
So, hopefully someone smarter than I and can state “Dummy, the shell file has an error on line…”
I am looking forward to being schooled on this. Here is my shell:
#!/bin/bash
iptables example configuration script
Flush all current rules from iptables
iptables -F
Set default policies for INPUT, FORWARD and OUTPUT chains
iptables -P INPUT DROP
iptables -P FORWARD DROP
iptables -P OUTPUT DROP
Allow SSH connections on port 22
This is essential when working on remote servers via SSH to prevent locking yourself out of the system
#iptables -A INPUT -p tcp --dport 22 -j ACCEPT
iptables -A INPUT -p tcp --dport 22 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp --sport 22 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 22 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 22 -m state --state ESTABLISHED -j ACCEPT
Block specific ip-addresses
iptables -A INPUT -s “x.x.x.x” -j DROP
Set access for localhost
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
Accept packets belonging to established and related connections
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
Open Ports for ping
iptables -A INPUT -p icmp --icmp-type echo-request -j ACCEPT
iptables -A OUTPUT -p icmp --icmp-type echo-request -j ACCEPT
iptables -A OUTPUT -p icmp --icmp-type echo-reply -j ACCEPT
iptables -A INPUT -p icmp --icmp-type echo-reply -j ACCEPT
Open Ports for DNS
iptables -A OUTPUT -p tcp --dport 53 -j ACCEPT
iptables -A INPUT -p tcp --sport 53 -j ACCEPT
iptables -A OUTPUT -p udp --dport 53 -j ACCEPT
iptables -A INPUT -p udp --sport 53 -j ACCEPT
Open Ports for FTP
iptables -A INPUT -p tcp --dport 20 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp --sport 20 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 20 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 20 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --dport 21 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp --sport 21 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 21 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 21 -m state --state ESTABLISHED -j ACCEPT
Open Ports for HTTP and HTTPS
iptables -A INPUT -p tcp --dport 80 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --dport 443 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp --sport 443 -m state --state ESTABLISHED -j ACCEPT
Prevent D0S attacks
iptables -A INPUT -p tcp --dport 80 -m limit --limit 25/minute --limit-burst 100 -j ACCEPT
iptables -A INPUT -p tcp --dport 443 -m limit --limit 25/minute --limit-burst 100 -j ACCEPT
Open Ports for SNMP
iptables -A INPUT -p tcp --dport 161 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp --sport 161 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 161 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 161 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --dport 162 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p tcp --sport 162 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 162 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 162 -m state --state ESTABLISHED -j ACCEPT
Open Ports for OpenFire
iptables -A INPUT -p tcp --dport 5222 -m state --state NEW,ESTABLISHED -j ACCEPT # Client to Server
iptables -A OUTPUT -p tcp --sport 5222 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 5222 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 5222 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --dport 5223 -m state --state NEW,ESTABLISHED -j ACCEPT # Client to Server SSL
iptables -A OUTPUT -p tcp --sport 5223 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 5223 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 5223 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --dport 5229 -m state --state NEW,ESTABLISHED -j ACCEPT # Flash Cross Domain
iptables -A OUTPUT -p tcp --sport 5229 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 5229 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 5229 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --dport 9090 -m state --state NEW,ESTABLISHED -j ACCEPT # Admin Console
iptables -A OUTPUT -p tcp --sport 9090 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 9090 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 9090 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --dport 9091 -m state --state NEW,ESTABLISHED -j ACCEPT # Admin Console SSL
iptables -A OUTPUT -p tcp --sport 9091 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p udp --dport 9091 -m state --state NEW,ESTABLISHED -j ACCEPT
iptables -A OUTPUT -p udp --sport 9091 -m state --state ESTABLISHED -j ACCEPT
iptables -A INPUT -p tcp --dport 5269 -j ACCEPT # Server to Server
iptables -A INPUT -p tcp --sport 5269 -j ACCEPT
iptables -A OUTPUT -p tcp --dport 5269 -j ACCEPT
iptables -A OUTPUT -p tcp --sport 5269 -j ACCEPT
iptables -A INPUT -p udp --dport 5269 -j ACCEPT
iptables -A INPUT -p udp --sport 5269 -j ACCEPT
iptables -A OUTPUT -p udp --dport 5269 -j ACCEPT
iptables -A OUTPUT -p udp --sport 5269 -j ACCEPT
Save settings
/sbin/service iptables save
List rules
iptables -L -v