Hello
I want to set openfire so that users can connect to it only from one IP.
In this way, I have a vpn server and users first run their vpn (the software used in phones is openvpn) and after connecting to the vpn server, they run the conversation software and can send messages to each other. to send
That is, if the users are behind a VPN
If you are running Openfire on a VPS that has a external IP you might use the firewall (ufw) to do it like this.
sudo ufw allow from 1.2.3.4 to any port 5222
where 1.2.3.4 is the external IP of your VPN.
or you can also use the internal IP of your VPN with /24 at the end.
i just gave you some generic way. i can think many ways to do it but we would have to know exactly details of your setup.
I agree with zoidberg. This seems like a job for something that’s external to Openfire, like a firewall.
Hello
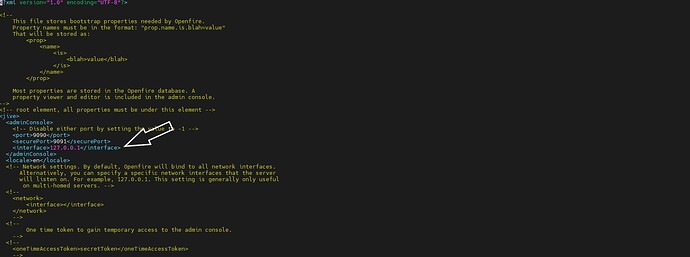
This cannot be done in the part specified in the photo in the openfire.xml file. That is, should I put the IP address of the VPN server in the interface section?
Is there a way to do these settings in openfire itself?
Thanks
In which vps should I run this command?
In the vps that I installed the openvpn service? Or vps that I installed the openfire service?
please guide me
that setting is to limit the Admin panel only. which is of course a good idea to protect your Admin panel to Lan only or trusted IPs only. however this is not what you asked for. you asked for to limit access to everyone using your XMPP server. to only allow the use of your XMPP server from a single IP (the VPN one).
the command should be run on the Openfire server machine. however be aware you will be messing up with eveything else too. for example if people can only use your server from the VPN ip, then why to even bother to have the Pionturn working? if lets say everyone is inside the same VPN within the same subnet they will not need any TURN server helping.
You will also need to adapt other ports too for example httpupload plugin will also need to be made with the same rules as of your 5222 and so on.
Hi, thanks for your reply
Yes, you got it right. I want all people to connect to openfire only through the vpn server (that is, run the openvpn program on their phone and when they connect to the vpn server, they can connect to the openfire server) and then be able to send their messages there. It means that all users connect through VPN and all connections are tunneled.
Now with these explanations, should I open all the ports that openfire needs in the vpn server?
If there is another way, please tell me.
Thanks
If your Openfire server wants to ONLY be accessible by the VPN do the following:
- Default block all, this tends to be the most secure way of “defaulting” a firewall, anything not explicitly allowed will be dropped.
- If you want the openfire server to be connected to from other XMPP servers (aka you plan to federate) you will need to allow connections from anywhere to the Openfire server on the s2s port you have configured.
- Allow connections to the c2s port, http/bosh port (unless you have a reverse proxy, instead permit it from there) and anything else you want clients to be able to access, but ensure the “from” address is specified to the IP address(es) of the VPN server, that way only the VPN server can connect to Openfire client port(s), as a VPN server acts a tunnel, anyone connected to the VPN should be able to access Openfire, but nobody else should. You do need to bare in mind, if your VPN server allocates globally addressable IP addresses to the clients, you will need to explicitly allow these in the rule, if it NAT’s the packets to its own address, then you only need to allow the VPN server address.
Unfortunately this is very much “Your Millage May Vary” (YMMV), as the configuration is entirely dependent on your specific circumstances.
Good luck.
Hello
The vpn server address is 192.168.10.10
And the openfire server address is 192.168.10.20
I entered the following command in openfire server
sudo ufw allow from 192.168.10.10 to any port *** proto tcp
that instead of the star, I put the required ports of openfire
After this, I could not connect to the openfire server in the mode without vpn. But after I run vpn, I was able to connect to openfire.
Did I do the steps correctly?
If you have any other suggestion, please let me know so that I can increase the security
Thanks
In the Openfire Management Console, click on the Server Tab, then the Server Settings Tab, and scroll down to Registration and Login.
Go down to Restrict Login, and enter the IP you want to allow connections from in the box labeled, " **Restrict ALL (including anonymous) logins to these IP’s:"
That will cause Openfire to only allow access from that IP. I do this on my Cloud Based installation of Openfire so that my 4 satellite office can all access the server, but no one else can.
@Brandon20 This only eliminates LOGIN from other IP addresses, this does not block other addresses from connecting to the server.
If the server only wants to be accessible from behind the VPN it should be done by the firewall, and not by the server.
Did I do the steps correctly?
@Gampo_Roka Yes, looks good.
Bare in mind blocking all ports from outside the VPN prevents other XMPP servers connecting to yours, you will not be able to federate now (aka, you can’t talk with people from other servers). If you want to be able to talk to other people on other servers, but only allow connecting to the server through the VPN, allow connections to the S2S port from anywhere, but block all the other ports from anywhere.
You can also use Brandon20’s suggestion as an additional line of defense, but the firewall should block it all and the rules in Openfire should never need to be used.
Good luck ![]()
Thanks for the reply friends
All users are on the same server and we don’t have another openfire server and we don’t want to connect to another server or other openfire servers to connect to our server.
All users are on the same server
Thanks
Hello
According to the information I have said about the servers in this post,
https://discourse.igniterealtime.org/t/question-about-how-to-limit-the-connection-to-openfire-server/93712/9?u=gampo_roka
The private IP of openvpn server is 10.8.0.1. In order to want users to connect to the openfire server only through this IP, what command should I use?
All users are on the same server and we don’t have another openfire server and we don’t want to connect to another server or other openfire servers to connect to our server.
All users are on the same server
It isn’t about connecting to other Openfire servers, that would imply clustering.
My point was that any user on your server will not be able to message anyone outside of that server… in fact you might want to block the s2s port outbound to prevent your openfire server from federating, this can also be configured within the web interface, but doesn’t hurt to make it a firewall rule too.
To do this Openfire side, go to Server/Server Settings/Server to Server/Allowed to Connect, and change it from Anyone to White List, leave the White List box blank, and this should prevent your XMPP server from connecting to other ones.
Do bare in mind, this setup means any other server will not be able to communicate with yours… for example you will not be able to use your openfire server (or your account on it) to connect to the igniterealtime MUCs for support, because that would require federation with igniterealtime, and this is what you are disabling.
Hope that clarifies a little more.
The private IP of openvpn server is 10.8.0.1. In order to want users to connect to the openfire server only through this IP, what command should I use?
I believe you already did this, you block all inbound traffic on the Openfire server, and then you only allow inbound connections on the c2s port from the IP address of your VPN server, this therefore will block all attempts to connect from any other IP address.
Hope that helps.
Hello and thanks for your reply
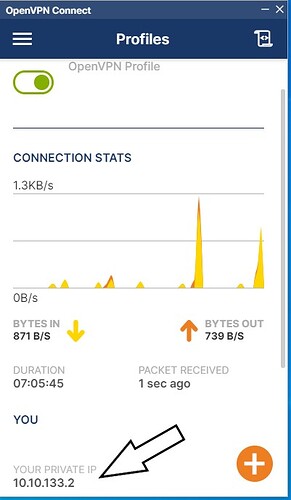
I mean the openvpn private IP that I showed in the picture
I want users to be able to connect to port 5223 and other openfire ports only through openvpn private IP.
Thanks
If Openfire is not running in the same network as the VPN, you must allow the VPN external IP address.
Didn’t you already do this here: Question about how to limit the connection to openfire server - #9 by Gampo_Roka
I am confused what you are asking?
I will take a wild guess and say the arrow pointing to your private IP is what you are confused about, I do not know your server infrastructure so I will give my best guess on what is going on.
OpenVPN creates an encrypted tunnel between your device and the server, in order for two devices to communicate they must have an IP address. Your VPN server is likely configured to have its own local network which is only accessible via the OpenVPN tunnel. 10.0.0.0/8, which is the address block which your private IP is allocated within, is part of RFC1918 which is a definition of all the IPv4 private address blocks. These are not globally routable thus are used for internal networks.
Your device is connecting to OpenVPN, and like a router, OpenVPN is sending you back an IP address and a DNS server to use (hopefully the DNS server is an address on the VPN network, so that you aren’t leaking DNS resolutions). Your device is being told its IP address is 10.10.133.2, the default gateway (where the traffic is sent) is likely the private IP address of the OpenVPN server… (I assume from the address sent to you from the OpenVPN server it is 10.10.133.1)
When the VPN server communicates with anything else, it NATs your packets, changing the IP address in the header to the external IP address of the VPN server, which is what you added to your Openfire firewall.
So your IP address, for all intended purposes apart from the OpenVPN network is the IP address allocated to the OpenVPN server, which according to the above is 192.168.10.10.
I hope that clarifies things, I am not the best at explaining.
thanks for your answer
If possible, I wanted to define the same Ip nat in the openfire server
Thanks for your tips
I am confused what you are asking…
Thanks to all friends who answered